Cloudflare Security

Intro
In our previous article we showed how to deploy a website on Cloudflare easily using Cloudflare Workers and Pages (cloudflare-workers-and-pages). When we deployed that site we linked a domain hosted on Cloudflare to that site. In this article, I will show you the security features that come built-in to a domain hosted on Cloudflare.
Cloudflare comes packed with several website security features that ready out of the box to secure your site. You can secure your traffic with TLS certificates, protect your site against common web attacks and bots, and even protect your API endpoints.
Under attack mode
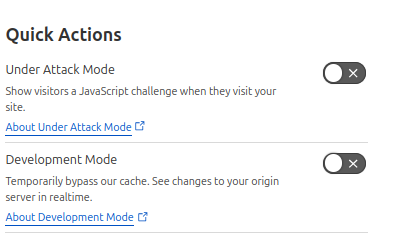
Before we go into all the different security features on Cloudflare, we should start at one feature that can be extremely helpful to any website owner. The "Under attack mode" is a feature that can be used if your website is under a large scale attack such as a DDoS or Bot attack and you want to protect your site while you investigate.
Under attack mode forces all users connecting to the site to go through a captcha or javascript based challenge. You may have seen this at one time or another when surfing a website and running into a "Verify your a human" challenge. If the site was on Cloudflare, its possible they were protecting themselves at that time from a larger scale attack.
To turn on "Under attack mode", navigate to the Overview menu of your site and look on the right hand side bar under "Quick Actions". Slide the button to "ON" and your all set. Cloudflare will now challenge each unique user to your site and protect you from further attacks. While your site is being protected, you might want to look next at the Security Analytics to discover what you can do to stop these attacks.
Analytics
On the Security > Analytics menu page, you can review statistics and events on suspicious or blocked traffic. Right at the top of the page, Cloudflare will list out suspicious activity against your site. Further down you can check out statistics like Top source IPs, top device types, etc. On the Events tab, you can find a list of blocked and mitigated attacks against the website.
Security Settings
Cloudflare domains have a several security settings enabled by default and ready out of the box. Best of all, these are available even on free accounts. The following are a list of common settings.
- DDoS protection
- Web application firewall
- Bot protection
- API protection
- Client-side abuse protections
DDoS Protection
DDoS (Distributed Denial of Service) protection is enabled by default and protects your site against high volume attacks. Because Cloudflare runs a global network with multiple points of presence they are no stranger to high volume level attacks such as DDoS. Cloudflare advertises having 388 Tbps of capacity, 23x the largest recorded DDoS attack. With such capabilities, Cloudflare is well positioned to absorb and mitigate even the largest attacks.
Managed Web Application Firewall
Web application exploitation protection (a.k.a Web Application Firewall) is enabled by default even on free subscriptions. The base feature set includes a managed signature ruleset that protects against common web application attacks. It also includes 5 custom security rules, 1 custom list, and 1 rate-limiting rule. If you upgrade to a Pro subscription additional features such as OWASP based signature rulesets, 20 custom security rules, 2 rate limiting rules, and an exposed credential check become available.
Custom Security Rules
Using custom security rules, you can add custom rules based on elements in the request and written using an expressive syntax. Define rules to block, challenge, or skip traffic based on key attributes such as HTTP headers and parameters, IP address, geo-location, and more. Rate-limiting options also allow you to define criteria to rate-limit traffic to your site.
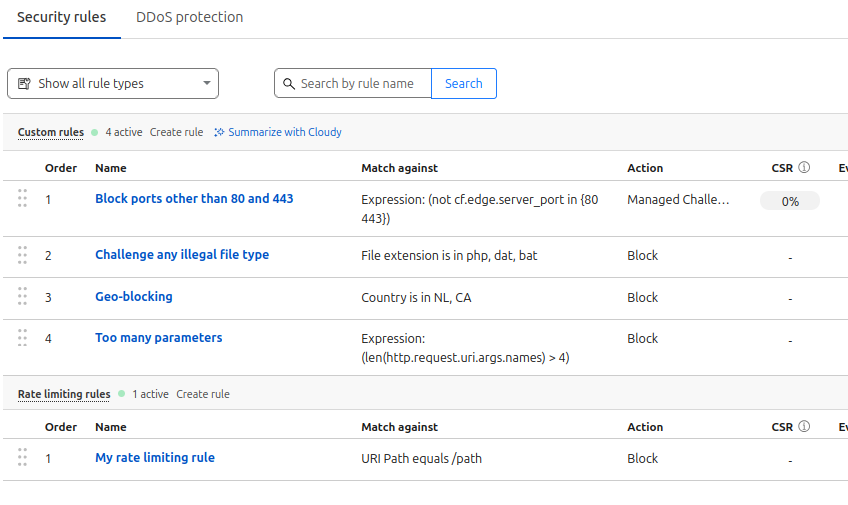
A few examples of the types of rules you can create. You can build all sorts of rules using simple filters or more complex expressions.
Bot Fight Mode
Bot Fight Mode is a simple one-click feature that can challenge bots attempting to access your website. This can prevent automatic scrapers and spammers. The free version Bot Fight Mode is not customizable. In order to customize the bot types that you can block/allow to your website, upgrade to a Pro subscription so you can enable "Super Bot Fight Mode". More than just a clever name, Super Bot Fight Mode integrates with your WAF custom rules to allow you to "Skip" particular types of bots based on varying criteria.
API Abuse
The API Abuse feature can be used to secure your APIs. By adding a schema definition you can validate all traffic to your API conforms to that schema. Anything that falls outside of the schema definition can be blocked or mitigated. Rules can be crafted based on each endpoint in your API and the specific parameters of those endpoints.
Client Side Security
Client side security can be maintained with Page Shield, a feature that can protect your site against malicious client side scripts and other attacks. Page Shield will monitor the scripts, cookies, and domains that the client side is interacting with. Through a set of Machine Learning algorithms they are able to tell if requests sent by the scripts have a probability of being malicious.
Certificates and TLS
One of the nice things about Cloudflare is the automatic SSL/TLS encryption and certificate management built-in. On the SSL/TLS Overview page, set your encryption mode to Full and everything is taken care of. A Let's Encrypt certificate is defined for your site and all requests are automatically set to HTTPS. Cloudflare supports several other certificate and TLS features also.
Origin Server certificates
Origin Server certificates are handy if you want Cloudflare to manage the TLS certificates between Cloudflare and your origin servers. This takes some of the complexity out of managing TLS certificates on your origin servers. You won't have to manage the process of procuring a public certificate from a public Certificate Authority (CA) and then managing its renewals and updates. Cloudflare provides an API that allows you to use them as your trusted CA and they will manage the certificates for you.
Client certificates
The Client certificates section manages mTLS connections, so you can provide client certificates for applications to access your site or API. Anyone without a client certificate will not be able to connect. Great for high-security scenarios when you want to be certain the client is an authorized device or application.
Edge certificates
The Edge certificates section manages all the details of your TLS connection between Cloudflare and your site's visitors. Some recommendations to use here are:
- Update minimum TLS to 1.2
- Set Always use HTTPS
- Enable TLS 1.3
- Turn on Automatic HTTPS Rewrites
Plan Tiers
Cloudflare comes with various subscription tiers. The tier that you select affects the security features that are available on your site. The following tiers are available on their site as of the publish date of this article.
- Free
- Pro
- Business
- Enterprise
Obviously the Free subscription is going to be the most limited in its features. For instance, on a free subscription you only get 5 custom security rules and 1 rate limiting rule. The number increases as you go up the tiers. Also the Free WAF Managed Ruleset only has a subset of the total rules that are in the paid version.
Some features limit the customization of rules like Bot and DDoS protection. While other features are simply not available at all (Page Shield and Mutual TLS) until you license to a certain tier. For more details on the specific feature limitations you can look at the Cloudflare plans page for a list of comparisons.
https://www.cloudflare.com/plans/
Summary
In Summary, Cloudflare features a comprehensive set of security features out of the box with few configurations required in most cases. Basic protections are available on free plan tiers that aren't too shabby. For a basic website having DDoS and Bot protection, basic WAF rules, and the availability of Under Attack mode as a starter is pretty decent.



